This article modifies the AWS Go CDK "static-site" example, found here. This example demonstrates how to host a static site in an S3 Bucket and serve content using a CloudFront Distribution. It also allows you configure a Route 53 subdomain in an existing Hosted Zone that you control. The subdomain will be pointed to the CloudFront Distribution to access the static content.
The example above was modified with the following with the following: 1) to be redeployable without having to destroy the stack 2) to add DNS records to a hosted zone with Route53 for a CloudFront distribution and 3) to modify the CloudFront default behaviors.
I found a CloudFormation example that has these configurations integrated, shown in the Sources section, that I could use to help me modify the Go CDK stack.
Introduction
This CloudFormation stack shows how to store and deliver static content using Amazon Simple Storage Service (S3) and Amazon CloudFront. This stack will also add Route 53 DNS records for mapping a custom domain to a CloudFront Distribution. An Amazon Certificate Manager SSL/TLS certificate will also be created for securing the CloudFront Distribution and for restricting access.
Background Link to heading
The following provides background to various services as they relate to this article and the Infrastructure as Code (IaC) templates, i.e., CloudFormation and the GO CDK.
S3 Link to heading
There are advantages to using S3 to store static web content. S3 offers
serverless management, durable and highly available storage, and scalable data storage at a
low cost. An S3 Bucket can be specified as the target origin for a CloudFront Distribution.
Introduction to Amazon S3
CloudFront Link to heading
The benefits of using CloudFront as a content delivery network (CDN) are to
improve performance and reduce costs. CloudFront leverages
the AWS global private network for better performance. CloudFront caches content in
Edge locations and delivers it to users which provides a faster response.

Introduction to CloudFront
CloudFront is a service that allows companies to protect and restrict access to their
content over the
internet. It provides additional access restrictions like geo-restrictions, signed URLs, and
signed cookies. CloudFront also includes security features such as Origin Access Identity
(OAI), which restricts access to an S3 Bucket and its content to only CloudFront.
It cab integrate with AWS WAF and AWS Shield to provide protection against malicious
exploits
and
DDoS attacks. AWS WAF allows control over access to content based on specified conditions,
while AWS Shield provides automatic protection against DDoS attacks. Customers can also opt
for AWS Shield Advanced for deeper insights, enhanced mitigations, and cost protections
against DDoS attacks.
Route53 Link to heading
Amazon Route 53 is a highly available and scalable Domain Name System (DNS) web service. You
can use Route 53 to perform three main functions in any combination: domain registration,
DNS routing, and health checking.
After you register a domain name, Route 53 automatically creates a public hosted zone that
has the same name as the domain. To route traffic to your CloudFront Distribution, you
create records,
also known as resource record sets, in your hosted zone. Each record includes information
about how you want to route traffic for your domain.
Introduction to Route53
CertificateManager Link to heading
AWS Certificate Manager (ACM) handles the complexity of creating, storing, and renewing
public and private SSL/TLS X.509 certificates and keys that protect your AWS websites and
applications. This might be required for HTTPS redirects.
Introduction to ACM
CloudFormation Stack Link to heading
Architecture
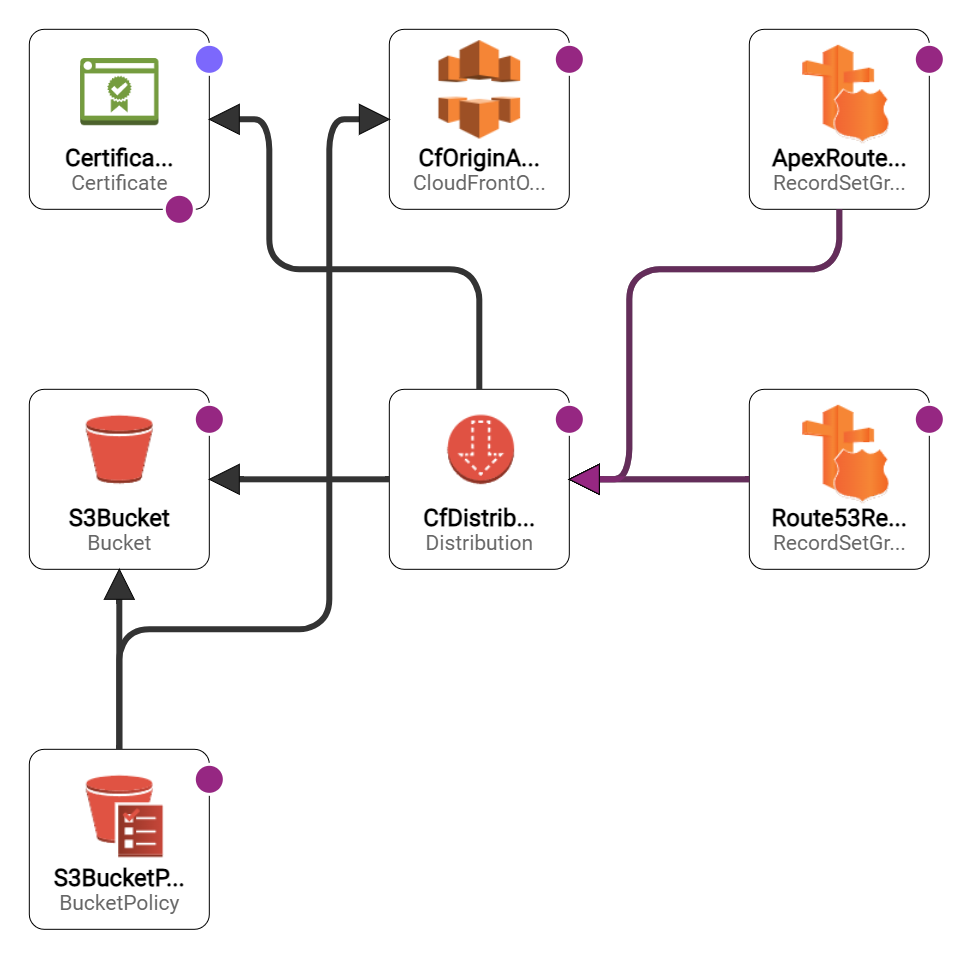
This CloudFormation stack shows how to store and deliver static content using Amazon Simple Storage Service (S3) and Amazon CloudFront. This stack will also add Route 53 DNS records for mapping a custom domain to a CloudFront Distribution. An Amazon Certificate Manager SSL/TLS certificate will also be created for securing the CloudFront Distribution and for restricting access.
CloudFormation Template Link to heading
In the Parameters section of the CloudFormation template, the HostedZone Info (SubDomain, DomainName, and HostedZoneId) and BucketName are parameterized in the CloudFormation script. There is also a parameter CreateApex to control to various subdomains, i.e., www.example.com and example.com.
Under Resources in CloudFormation template, an S3 Bucket, S3 Bucket Policy,
and CloudFront Origin Access Identity (OAI) resources are created.
An S3 Bucket is created, and a S3 Bucket Policy is attached to
restrict access to the S3 Bucket only through CloudFront using an Origin Access
Identity, S3CanonicalUserId.
Under Resources in CloudFormation template, a CloudFront Distribution is also created.
Various settings for the CloudFront Distribution are set, i.e,
default cache behavior, specifying allowed and cached HTTP methods, cache compression,
time-to-live settings, and https redirects.
An alias for the distribution is set to ${SubDomain}.${DomainName}.
Under Origins, DomainName and Id are set to reference the S3 Bucket and
the S3 Bucket's domain name. The SSL Certificate is also specified to allow for
HTTPS redirects.
Under Resources in CloudFormation template, a Cerficate resource is created.
The variable CreateApexConfig, when set to true, allows for two domain names
to be secured by the certificate, i.e., example.com and www.example.com.
AWS Route 53 Record Set Group resources are created. This resource created DNS records in the Route 53 hosted zone. One resource is created for each subdomain configuration. The DNS records point to the CloudFront Distribution using the AliasTarget property. This allows you to associate your domain/subdomain with the CloudFront Distribution.
Go CDK Link to heading
The AWS CDK allows for Infrastructure as Code (IaC) to be defined programmtically. The CDK is used synthesize a CloudFormation template which can be deployed in the cloud.
The GO CDK script below seems to have a one-to-one parameter mapping with the
CloudFormation template above.
s3bucket is a parameter, defined in StackConfigs,
which is passed into the CDK's main() function. Note that cloudfrontOAI
provides the same functionality as CfOriginAccessIdentity.
For CloudFront's BehaviorOptions, there seemed to be less options available than using the CloudFormation template directly. The rest of the resources seem to have the same configurations available as the template. One benefit of using the GO CDK is that local files can be uploaded to S3 as part of the deployment process.
The s3deploy function allows for website-directory
to be deployed to the siteBucket resource, defined previously in the code,
during the CloudFormation stack deployment.